LanScope Cat Features
Manage your IT before it gets out of control.
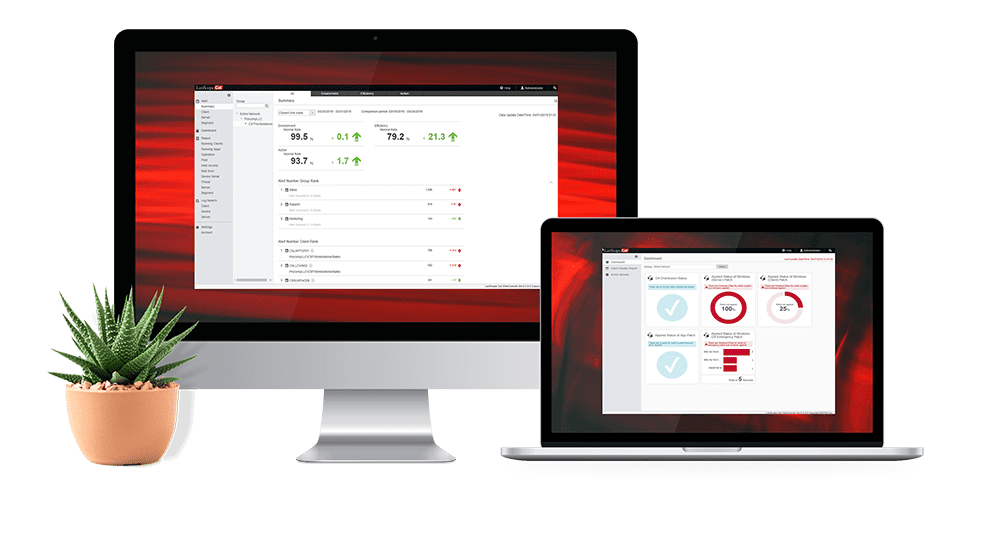
IT Asset Management
Never-before-seen visibility into the state of all assets
Your users buy new devices and apps, and access your network from anywhere, at anytime. Manage your IT before it gets out of control. LanScope Cat allows greater visibility into your assets and how users actually use them.

Access continual logging

Verify system updates and patches

Track license inventory and usage

Establish and enforce policies

Record printers and other peripheral devices


Identify permitted and forbidden apps
EMPLOYEE MONITORING
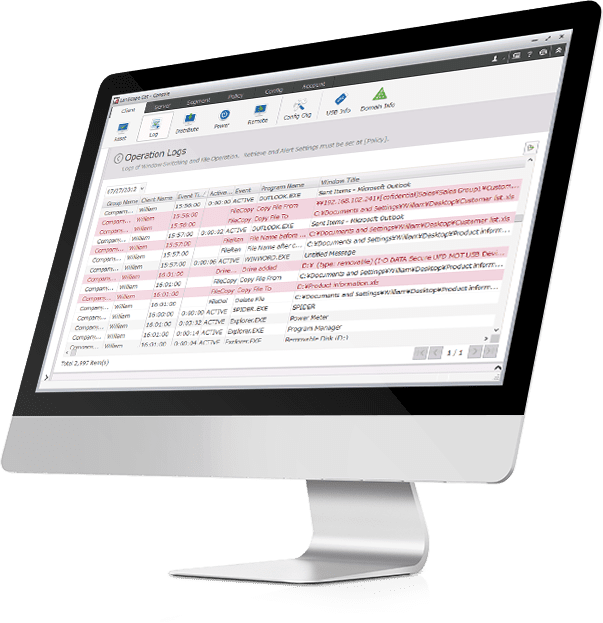
Know what’s really happening
User activity monitoring is complex, but LanScope Cat records “who” did “what” “when” on “which device” in one dashboard. If some operational violation that could be an information leak occurs, such as writing a customer list to a USB, a warning is displayed to the user, and the illicit operation is prevented. Monitor your onsite and remote workforce with LanScope Cat.
WEB Access MONITORING
Monitor web activity across the network
LanScope Cat makes web access management easy. View who viewed particular sites and for how long. Block certain sites and get alerted to policy violations.


Know Who Views What
Record website visit history and webmail usage.



Control What They Can View
Block certain sites or determine which users can access specific sites and for how long.


Know When Policy Is Broken
Get notified and set rules around uploads, downloads, blocked keywords and/or URLS.
IT Policy Enforcement
It’s only policy if you can enforce it
IT devices can typically be hard to manage and secure—and cause a host of problems for IT managers! LanScope Cat is able to lower the overall security risk by providing a solution to the age-old problem; LanScope Cat protects devices, applications, and data, while delivering actionable insights into user behavior.



Control the Use of Devices
Control USB/CD/FD/SD memory and/or other devices including Wi-Fi/Bluetooth connections and identify files are being copied to and from storage devices.


Set User Permissions
Allow certain users to use specific devices and/or prohibit read/write operations.


Take Corrective Action
See what is happening throughout your network so you can take immediate corrective action if needed.
MALWARE PROTECTION WITH CYLANCE
Proactively protect your network


LanScope Cat delivers advanced threat prevention combining world-class endpoint management with market-leading malware protection within a robust dashboard. Every device connected to the network is regularly scanned in an intelligent, nonperformance impacting process to ensure that all endpoints are continually protected by the current version of the Cylance agents.
Detect



Investigate



Mitigate
Ready for real-time notifications about suspicious network activity?